Report: Restrictions to circumvention tools in Venezuela

Importance of circumvention tools in the Venezuelan context
Venezuelans have been suffering from increasing levels of internet censorship for more than 15 years, with increasing limits on the tools used to circumvent it. Access to information and news, as well as their right of association, are curtailed by internet blocks against websites and platforms. Journalists, politicians, human rights defenders, activists and many other actors among the civil society are constantly being censored due to the government’s attempts to limit free speech online in a context where independent media in radio is scarce and censored, and practically nonexistent in printed press and TV.
The censorship is implemented by all major Internet Service Providers (ISP), normally under orders from the telecoms regulator CONATEL. However, the most extensive and sophisticated blocking is performed by the state-owned ISP, CANTV, the government has successfully blocked access to information using different techniques, from DNS blocks to SNI Filtering and DNS response injection, which was used in state-sponsored phishing attacks.
Just a few days ago VE sin Filtro reported new blocks to four news organizations that affected users in six different ISPs on top of 35 News sites being already blocked during a recent election. The limitations of human rights in the Venezuelan digital space are documented in the Freedom on the Net 2021 report, from Freedom House.
Current censorship of VPNs and circumvention tools
In order to have access to reliable information and avoid surveillance, Venezuelan citizens need to use different circumvention tools and strategies. The most effective has been the use of VPN services that allowed them to hide their identity and overcome internet blocks, despite attempts to limit them.
Changing the DNS servers used by a device is also a common technique, but it doesn’t work for many blocked sites, particularly on the state-owned CANTV.
TunnelBear
The block against TunnelBear continues on all major ISPs in Venezuela. It’s main website, tunnelbear.com, has experienced DNS blocks in addition to HTTP/HTTPS simultaneously by CANTV (AS8048) since 2019. The rest of ISPs in the country started a DNS block on August 20th, 2020.
TunnelBear can be downloaded from the app stores on both iOS and Android, the block mostly affects users wanting to know more and those trying to download it to their PC. The software can be downloaded on alternative URLs.
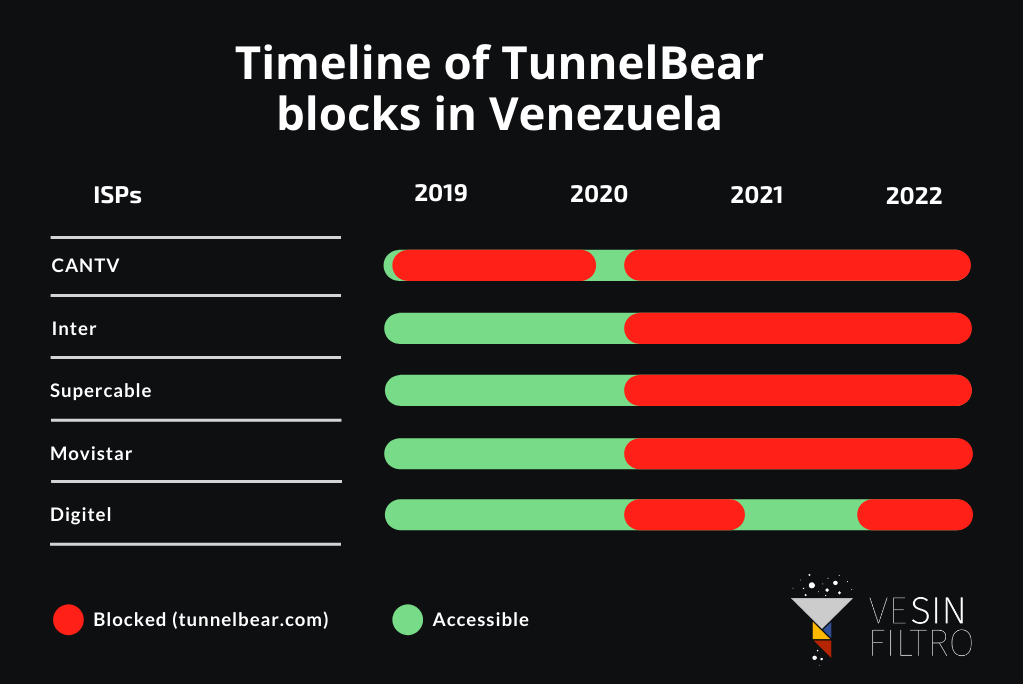
While these blocks don’t affect the VPN functionality itself, for a period of time in 2021 they prevented the registration of new users once the app was installed on the device, a required step to use the VPN. This was fixed after TunnelBear was made aware of this. Currently the blocks do affect TunnelBear users trying to change their passwords since that system relies on the accessibility to tunnelbear.com in order to work properly.
Psiphon
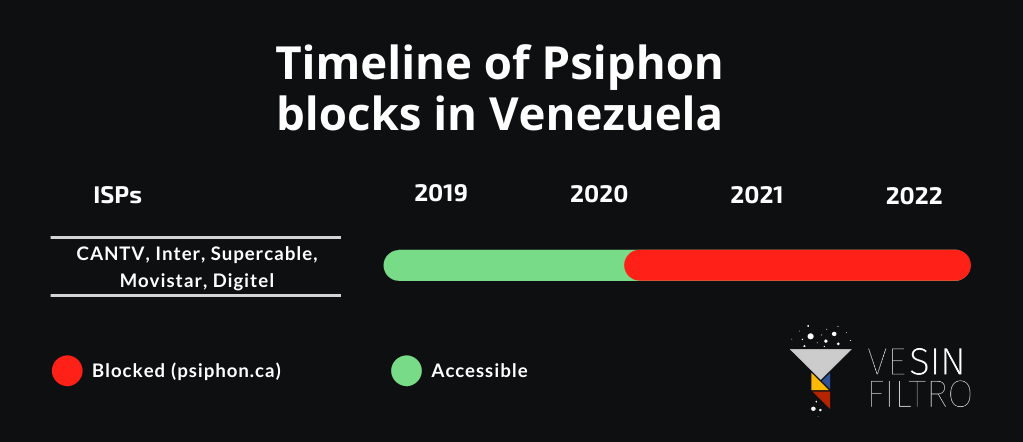
Psiphon’s main website, psiphon.ca, remains blocked by all major ISPs. In the state-owned CANTV the site is affected by an HTTP/HTTPS + DNS block, while in the rest of the ISPs is only affected by a DNS block. The site has been blocked in Venezuela since August 2020, after increased attention around blocks at the time and awareness campaigns.
These blocks don’t affect the VPN functionality in any way, nor does it compromise the normal user experience of Psiphon.
IKEv2 VPN Protocol
VPNs use different protocols to protect and anonymize an internet connection, one of them being IKEv2, which is built into many popular VPN providers such as Windscribe, Proton VPN, NordVPN, among others. During most —if not all— of 2021, users of CANTV couldn’t establish connections with any VPN service using the IKEv2 protocol, but by February 2022 this block was lifted. Incidentally, IKEv2 is now very rarely, if ever, the default protocol of VPN applications
Anonymouse.org
Anonymouse is a web proxy that can be used to circumvent censorship, however we strongly discourage its use, as it’s an unencrypted web proxy that poses important privacy and security risks. It was previously blocked in the state owned CANTV, but it’s currently only blocked by some private providers.
| Website | CANTV | Inter | NetUno | Supercable | Movistar | Digitel |
|---|---|---|---|---|---|---|
| psiphon.ca | DNS+HTTP/HTTPS Block | DNS Block | DNS Block | DNS Block | DNS Block | DNS Block |
| tunnelbear.com | DNS+HTTP/HTTPS Block | DNS Block | DNS Block | DNS Block | DNS Block | DNS Block |
| anonymouse.org | Accessible | Accessible | DNS Block | DNS Block | HTTPS block | DNS Block |
Tor blocking
Tor is a well-known tool that provides a high level of anonymity to internet traffic and circumvents internet censorship. We noticed an increase in the number of inaccessible bridges and directory authority relays from CANTV, similar but less effective than what happened almost four years ago.
This means that there is currently an active effort to block Tor connections in Venezuela, but it’s not very effective. According to the measurements gathered in the past few months, between 70% to 80% of Tor directory authorities are blocked at any given time in AS8048. In practice, Tor connections are successfully established most of the time, but it may take longer
The Venezuelan government has blocked Tor on CANTV in the past. In 2018 VE sin Filtro and OONI reported the blocking of Tor connections including many obfs3 and obfs4 public bridges, specially those that the Tor Browser has built-in by default. That time the block was much more effective, preventing users from connecting to the Tor network from CANTV most of the time.
This censorship against Tor operates using a TCP block to these known IPs or IP:Port pairs, similarly to what happened in 2018. Many publicly known bridges that were not built-in have been blocked.
Blocking and limiting of DNS servers
We monitor the behavior of different DNS servers on all the major ISPs, since changing to a trusted DNS server can mitigate the majority of blocks that internet users in Venezuela are constantly experiencing. The results that we obtained remain the same as what we shared in our last report regarding this topic.
| Public DNS | IP | CANTV | movistar | digitel | inter | supercable | NetUno |
|---|---|---|---|---|---|---|---|
| a.resolvers.level3.net. | 4.2.2.1 | OK | OK | Blocked | OK | OK | OK |
| b.resolvers.Level3.net | 4.2.2.2 | OK | OK | Blocked | OK | OK | OK |
| c.resolvers.level3.net | 4.2.2.3 | OK | OK | Blocked | OK | OK | OK |
| Cloudfare | 1.1.1.1 | OK | Blocked | Blocked | OK | OK | OK |
| Cloudfare | 1.0.0.1 | OK | OK | Blocked | OK | OK | OK |
| cns1.cw.net | 141.1.1.1 | OK | OK | Blocked | OK | OK | OK |
| Comodo Secure DNS | 8.26.56.26 | OK | OK | Blocked | OK | OK | OK |
| Comodo Secure DNS | 8.20.247.20 | OK | OK | Blocked | OK | OK | OK |
| DNS Advantage | 156.154.70.1 | OK | OK | Blocked | OK | OK | OK |
| DNS Advantage | 156.154.71.1 | OK | OK | Blocked | OK | OK | OK |
| dns-fra.de.ignite.net | 195.182.110.132 | OK | OK | Blocked | OK | OK | OK |
| dns-muc.de.ignite.net | 62.134.11.4 | OK | OK | Blocked | OK | OK | OK |
| dns1.nyc.dns-roots.net. | 208.78.24.238 | OK | OK | Blocked | OK | OK | OK |
| Dyn | 216.146.35.35 | OK | OK | Blocked | OK | OK | OK |
| Dyn | 216.146.36.36 | OK | OK | Blocked | OK | OK | OK |
| Google DNS | 8.8.8.8 | OK | OK | OK | OK | OK | OK |
| Google DNS | 8.8.4.4 | OK | OK | Blocked | OK | OK | OK |
| Open DNS | 208.67.222.222 | OK | OK | Blocked | OK | OK | OK |
| Open DNS | 208.67.222.220 | OK | OK | Blocked | OK | OK | OK |
| Quad 9 | 9.9.9.9 | OK | OK | Blocked | OK | OK | OK |
| Quad 9 | 149.112.112.112 | OK | OK | Blocked | OK | OK | OK |
| Yandex | 77.88.8.8 | OK | OK | Blocked | OK | OK | OK |
| Yandex | 77.88.8.1 | OK | OK | Blocked | OK | OK | OK |
| Yandex Family | 77.88.8.7 | OK | OK | Blocked | OK | OK | OK |
| Yandex Family | 77.88.8.3 | OK | OK | Blocked | OK | OK | OK |
| Yandex safe | 77.88.8.88 | OK | OK | Blocked | OK | OK | OK |
| Yandex safe | 77.88.8.2 | OK | OK | Blocked | OK | OK | OK |
| cns2.cw.net | 195.27.1.1 | OK | OK | Blocked | OK | OK | OK |
| uneeda.telstra.net | 139.130.4.4 | OK | OK | Blocked | OK | OK | OK |
Digitel
Our tests covered a list of 30 DNS servers, all of which were blocked by Digitel, with the exception of the most well-known one, 8.8.8.8, Google’s Public DNS server.
Digitel blocked any UDP or TCP traffic on port 53, regardless of their content or application-layer protocol. Requests to these servers from other ports worked when available, with the exception of connections to Google’s 8.8.8.8 that weren’t blocked at all.
We can conclude that, with the exception of the server 8.8.8.8 by Google, and DNS servers used internally, all other standard DNS services are blocked to Digitel users.
Movistar
In the case of Movistar, 1.1.1.1, the main public DNS server of Cloudflare and APNIC, is inaccessible. Given that the rest of the most popular DNS, including Google’s 8.8.8.8, do not present censorship, it is very likely that this is not a case of censorship but rather an internal operations conflict with the IP address 1.1.1.1 by Movistar.
The Cloudflare 1.0.0.1 alternate DNS server is fully functional as well as the Cloudflare’s mobile app called “1.1.1.1”.
CANTV
While no blocking of public DNS servers was observed, VE sin Filtro has documented two separate instances of DNS response injection by CANTV in 2019 and 2020. In those instances it was used to impersonate third party servers and forge a response pointing politically sensitive domains to malicious servers, as part of a state-sponsored phishing campaign. This demonstrates interest and the capacity to interfere with DNS requests performed to any server on the internet. Future DNS manipulation or blocking of external DNS resolvers should be considered a significant risk for CANTV users.
DoH and DoT
Considering the above, the use of DNS over TLS (DoT) and DNS over HTTPS (DoH) are recomendable when possible for added privacy and security, in addition to selecting an external DNS of your choice. On all ISPs DoT and DoH worked, with the exception of address 1.1.1.1 on Movistar that was unreachable for any kind of traffic.
| CANTV | Movistar | Digitel | Inter | NetUno | Supercable | |
|---|---|---|---|---|---|---|
| DoT | Not blocked | Not blocked, except 1.1.1.1 | Not blocked | Not blocked | Not blocked | Not blocked |
| DoH | Not blocked | Not blocked, except 1.1.1.1 | Not blocked | Not blocked | Not blocked | Not blocked |
Methods
The assessment of blocked websites was performed by analyzing OONI web connectivity network measurements produced periodically from multiple vantage points as well as other ad-hoc tests.
Tor blocking was analyzed using OONI Tor measurements produced periodically from different vantage points, tests provided by The Tor Project and ad-hoc tests.
The operation of different tools and apps was verified by running the apps on different days, from different vantage points using different configurations and manually evaluating any problems.
Recommendations
We recommend Venezuelan internet users to have at least one VPN installed and tested on personal devices such as cell phones and computers, even if it’s not planned to use them immediately.
The VPN we recommend the most is Psiphon, but Tunnelbear is also a good option that is very easy to use. To download them from Venezuela you can use the following alternative links that until the date of publication have not been blocked:
Psiphon:
-
psiphon3.com
-
Android: Play Store
-
iOS: Apple App Store
-
Proxy: https://58685.info
-
E-mail: get@psiphon3.com
Tunnelbear:
-
Android: Play Store
-
iOS: Apple App Store
-
tuneloso.com
We recommend using a trusted VPN, especially when accessing websites with political content or participating in online activities that may be in conflict with the ruling party in Venezuela. Additionally, a VPN allows you to access blocked websites and media.
If you use Tor in Venezuela it’s advisable to note down a list of additional bridges that are possibly not blocked, to configure in Tor browser and to familiarize with how to use Pluggable Transports in Tor Browser.
Estas son nuestras recomendaciones para evadir #bloqueos en #internetVE:
— VE sin Filtro (@vesinfiltro) March 31, 2021
Aunque la página de @PsiphonEsp y @theTunnelBear estén bloqueadas en #CANTV, estos siguen siendo nuestros VPN recomendados.
🧵Más info en este hilo: pic.twitter.com/SFmRM00olQ
It is not a bad idea to change DNS servers, as long as you are aware that this does not help you bypass all the blocks in Venezuela or protect you from sophisticated DNS manipulations that the Government of Venezuela has used against its citizens. There are many public DNS options, among them the most recognized are: 8.8.8.8 and 8.8.8.4 (Google); 1.1.1.1 and 1.0.0.1 (Cloudflare and APNIC); or 9.9.9.9 and 149.112.112.112 (Quad 9). To know how to change the DNS of your computer or mobile device, you can check this link.